Published for International Legal Technology Association on 1/2/2020
On January 15th, Microsoft will be releasing a new version of Microsoft Edge built on Chromium to all supported versions of Windows 10. This new version of Edge Chromium also supports Windows 7, 8.1, and Windows Server. With this release, the legal vertical vendors will be able to stop supporting Internet Explorer. Read on to learn how to prepare for this new change.
Background
When Microsoft released Windows 10 in the summer of 2015, a new browser named Edge was introduced. This new browser replaced Internet Explorer (IE) 11, which Microsoft introduced in 1995 along with Windows 95. Those of us that have been in IT for a bit will remember the browser wars that started in the nineties. Internet Explorer since then has been the default browser in all Windows versions from Windows 95 and through Windows 8.1. IE has been through many upgrades and became bloated as Microsoft added more features and changed compatibility modes a few times. These changes were hard for many organizations to adopt. The rapid nature of change with HTML standards made it hard for legal vertical web sites to adopt to those changes and continue to support Internet Explorer.
With the introduction of Windows 10 and the new Edge browser, Microsoft hoped their new modern browser would compete with Chrome and Firefox. Unfortunately, that didn’t occur. Customers and 3rd parties did not want to invest in rebuilding sites to make them work in Edge.
Because of this, we have had many clients adopt Google Chrome or Firefox as their default browser regardless of Windows version as they knew those browsers on Windows 7, 8, or 10 and Windows Server (Citrix) would have the same experience (in most cases). Other firms chose to set IE 11 as their default while other firms chose Edge. This browser fragmentation caused many issues in the legal vertical.
Today
In late 2018, Microsoft announced that Edge would be redeveloped to use the open-source Chromium platform started by Google with contributions by a global community. The goal of the new Edge Chromium browser, targeted to be released in mid-January, is for more web compatibility (if the site works on Chrome, it should work the same on the new Edge Chromium). Edge Chromium allows for management via MDM, GPO, and endpoint management solutions like Microsoft Endpoint Configuration Manager which I will discuss later. Because the new Edge browser is based on Google’s Chromium platform, it had many of the Google services in the source. Microsoft has disabled or changed over 50 of them such as Google Now, Pay, Extension store, etc.
The full list of what has been disabled or replaced below:

How do we get it?
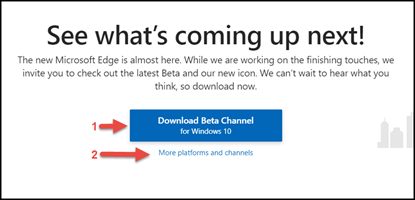
The official release target is January 15th, as of this writing. To start your testing today, you can join three types of Inside channels at https://www.microsoftedgeinsider.com.
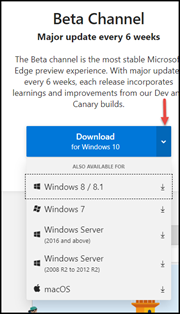
When you launch the site, the default download and the most stable release is the Beta Channel (#1 in the screenshot below). If you would like to try more up to date and frequent Channels update, as Microsoft develops then choose the More platforms and channels link on the site (#2 in the screenshot below). This link will give you access to a Dev Channel which is updated weekly and the Canary Channel which is updated daily. The Canary channel is usually released right after Microsoft updates the code, which is why it is called a Canary build. In the old mining days, a canary would be sent into a coal mine to check for deadly gas.
The channels are also available on other OS platforms. If you click the down arrow below the download button, you will see options for previous Windows client and server versions and macOS.
How do I deploy and manage?
If you are an organization that has automatic updates enabled in Windows 10, Microsoft will automatically deliver the new browser. I would not recommend this as you will want to enable change management and user experience to avoid confusion and calls to the help desk. For those environments, Microsoft has a blocker tool you can deploy to block Automatic Updates from installing on Windows. Please review the Microsoft site here for more information on this.
If you are a firm that has a system management solution like Intune, Configuration Manager (ConfigMgr), or other tools that manage the Microsoft Updates, you will have a little more control.
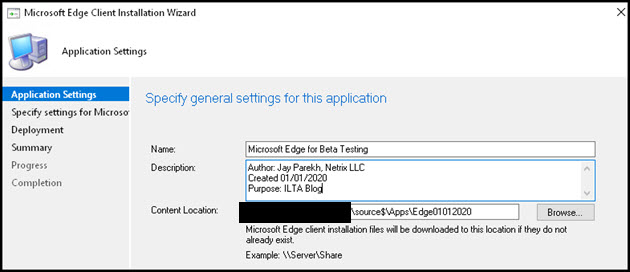
In Configuration Manager 1910, you can now manage Edge deployment. In ConfigMgr 1910, under Software Library, you now have Microsoft Edge Management node, and once you click that, you will have the option to Create Microsoft Edge Application.

Clicking the Create Microsoft Edge Application button, you will start the wizard, which is similar to many ConfigMgr dialogs.
The next option is to choose your Channel and version of Edge to deploy. After this, you will have the option to choose the deployment options (Collection, etc.), or you can create the package.

Once the package has been built, the source folder will have the files needed for x86 and x64 versions with a PowerShell script that will be used to call the installation in the Deployment Types.

In Application Management, under Applications, you will see your new application along with the Deployment Types. Just like any ConfigMgr application/package, you can deploy to the Collection of your choosing.

More information on using ConfigMgr is available here. If you are using Intune to manage Windows, you can read more about options here.
What if I don’t have Intune or Configuration Manager?
If you don’t have ConfigMgr and are using tools like Ivanti, Altiris, Quest (formally Dell) Kace, etc. you can create your package using the offline installer. These are full MSIs so you can use the MSI commands to silently deploy using the tool of your choice.
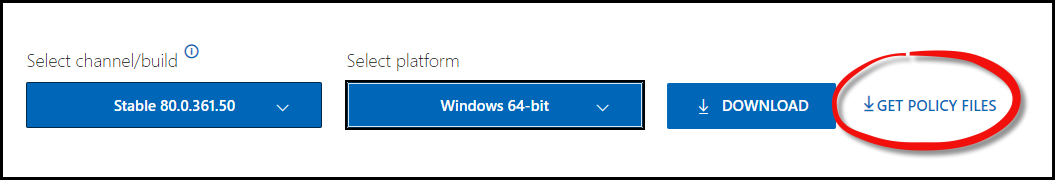
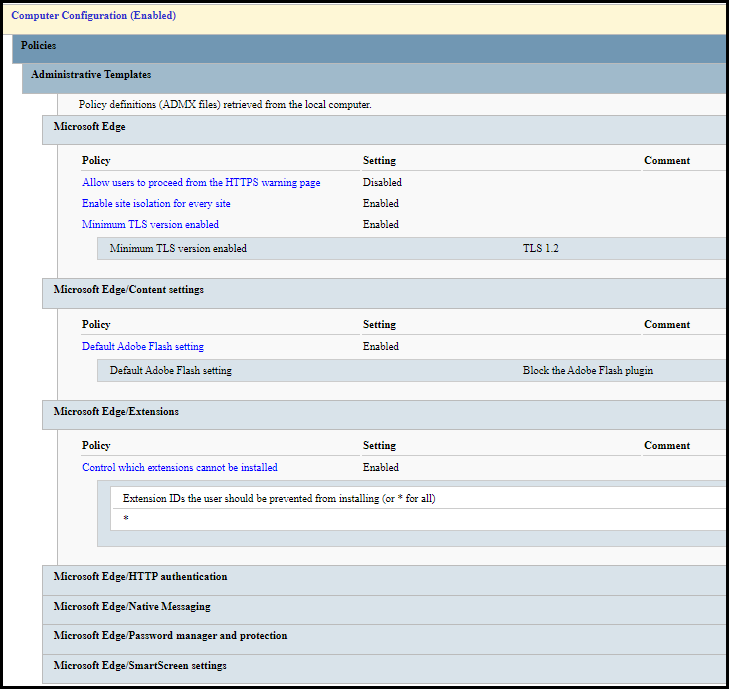
The configuration of the new Edge can be done through Group Policies for domain joined computers or via supported MDM solutions like Intune for non-domain or hybrid joined computers. For the group policy administrative templates, you can download via the same location as the offline installer.
We will have another series of written or video blogs that will discuss further configuration, management, and update options over the next couple of months.